-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
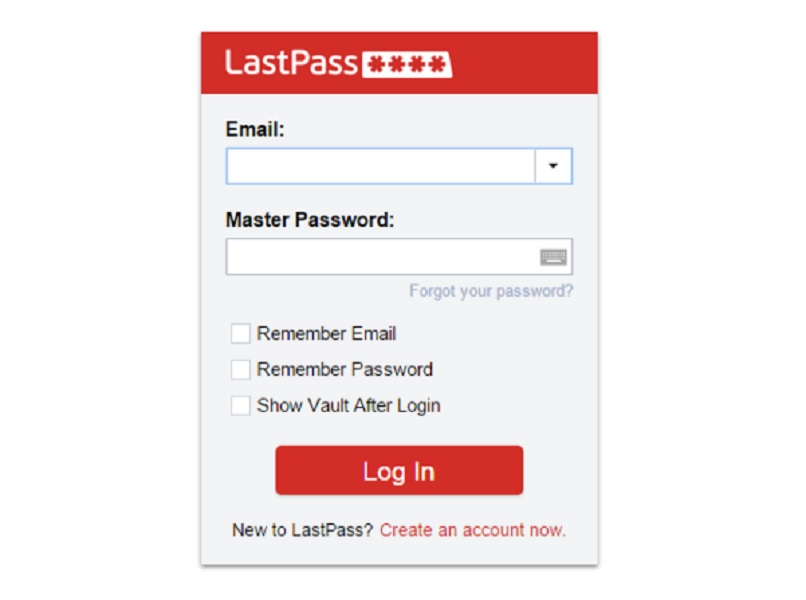
‘LostPass’ Phishing Scam Can Steal LastPass Credentials
During a presentation on Saturday at the ShmooCon hacker conference in Washington, D.C., Cassidy demonstrated how users can be fooled into submitting both their LastPass master password and their 2nd-factor authentication code to a malicious server using bogus pop-up notifications in the browser.
Advertisement
Like other password managers, LastPass allows users to store multiple login details for various sites and services, which they can then access using a single master password.
Mr. Cassidy developed a tool, which he also published on GitHub, called LostPass, which would be able to automate a simple phishing attack against LastPass users and harvest their password vault. Users can’t tell the difference between a fake LostPass message and the real thing because there is no difference. “Training is not effective at combating LostPass because there is little to no difference in what is shown to the user”. “It’s pixel-for-pixel the same notification and login screen”, Cassidy said in a blog post. The attacker’s server will check if the credentials are correct by calling LastPass’s API.
If the user is logged out of LastPass and visits a website to which LastPass holds the password, the browser displays a banner with a login button stating that “Your LastPass session appears to have expired”. “Our team is working to release additional notification options that bypass the viewport and therefore eliminate the risk that it presents in phishing attacks”, the company wrote in its statement.
The attack is not a vulnerability bug within LastPass itself, but highlights a major problem that could catch even the most careful users out, tricking them to give the attackers their login credentials.
It was previously a requirement for daredevils not using two factor. Cassidy said because the LostPass attack phishes users for their two-factor authentication data, the email confirmation was sidestepped. “He describes LastPass’s login workflow as complex and somewhat buggy”, and says that it was easy to detect LastPass and find the HTML and CSS code to mimic the service. According to Cassidy, the attack is most convincing for users operating the Chrome browser.
“By requiring verification for unknown locations or devices, we’ve ensured users are protected from this attack”, LastPass Marketing Manager Amber Gott Steel told TechNewsWorld.
Additionally, he also says that turning on IP restrictions for the LastPass paid version is better than using 2FA protection.
Moreover, the intruder can create a backdoor into the account through LastPass’s emergency contact feature, as well as disable two-factor authentication and add to the account a trusted device that belongs to the attacker, he noted. “We need to take a long look at phishing and figure out what to do about it. In my view, it’s just as bad, if not worse, than many remote code execution vulnerabilities, and should be treated as such”.
Cassidy managed to replicate the LastPass notification window in Chrome that asked for a Google Authenticator code.
Advertisement
LastPass said email verification will all but neuter the attacks unless email accounts are also compromised. LastPass has encouraged Google for years to provide a way to avoid using the browser viewport for notifications, ‘ LastPass explaiend in a statement.