-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
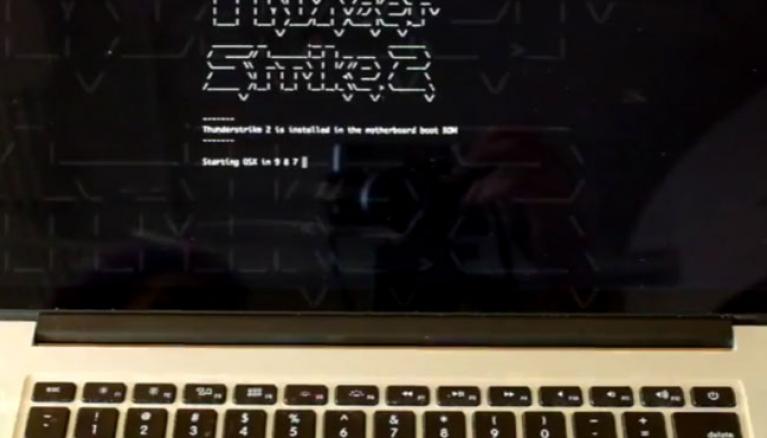
The only cure for new Apple malware is to trash your Mac
“[The attack is] really hard to detect, it’s really hard to get rid of, and it’s really hard to protect against something that’s running inside the firmware”, Kovah said. They used an Apple Thunderbolt to Gigabit Ethernet adapter to demonstrate how the malware can spread undetected, but an attacker could also infect the option ROM on an external SSD or on a RAID controller. Devices don’t even need to be networked for the worm to spread, and once it’s infected your machine the only way to remove it is to open up your Mac and manually reflash the chip.
Advertisement
Apple products have a reputation for being more secure than PCs. In fact, the researchers said five of the six vulnerabilities studied affect Mac firmware.
The Apple Mac firmware worm research was conducted by Kovah, owner of LegbaCore, a firmware security consultancy, and Trammell Hudson, a security engineer with Two Sigma Investments. But unlike Thunderstrike 2, the original Thunderstrike virus could only be spread via physical access through the peripherals.
They’re probably not going to present their findings at Black Hat and Def Con, like the creators of Thunderstrike 2 are.
The attack happens at the BIOS level and is targeted at the computer’s firmware.
Firmware runs when you first boot a machine; it launches the operating system.
“What we also found is that there is really a high likelihood that the vulnerability will also affect Macbooks”. For Apple computers, the firmware is called the extensible firmware interface (EFI). It can then target other devices plugged into your computer, like a USB stick, infecting the firmware of that device so that the worm continues to spread with each computer it is plugged into. Once a machine is booted with a worm-infected device inserted, the machine loads the option ROM from the device, which triggers the process for the worm to write its malicious code to the boot flash firmware.
One way to randomly infect machines would be to sell infected Ethernet adapters on eBay or infect them in a factory.
Once infected, the firmware will examine the Mac for connected peripherals that contain Option ROM. This could include Thunderbolt accessories. Apple has fixed one of them and partially patched another, but three security holes are untouched, the researchers told Wired. Kovah likened Thunderstrike 2 to the infamous Stuxnet worm that infected Iran’s uranium enrichment facilities a few years ago.
Advertisement
On Twitter, Hudson previously asked if you are “vulnerable to the cute kittens of Thunderstrike 2” and his tweet included a picture of a Mac with a cute kitty and a link to “download a cute cat screensaver”.