-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
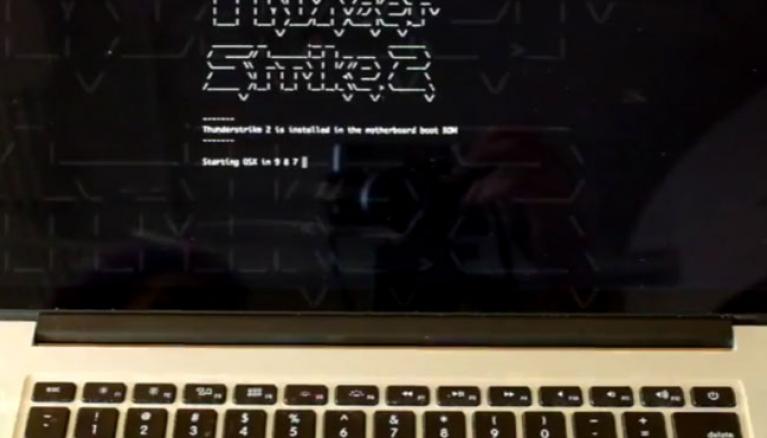
Researchers Create First Firmware Worm That Can Infect Macs
Apple even brought up its product’s resistance to viruses and malware in the famous line of Mac vs. PC commercials from the mid 2000s. Much like the sequel, Thunderstrike targeted Mac firmware and could not be detected. The hack developed by researchers Xeno Kovah and Trammell Hudson can attack the firmware of Macs and all top PC makers, according to Wired.
Advertisement
Thunderstrike 2 is different from its predecessor in that an attacker would not require physical access to a Macbook; this attack can be accomplished remotely and exploits self-replicate via peripherals, researchers said.
When another machine is booted with this worm-infected device inserted, the machine firmware loads the option ROM from the infected device, triggering the worm to initiate a process that writes its malicious code to the boot flash firmware on the machine.
Once attacker has the root control, they can exploit a vulnerability discovered by Rafal Wojtczuk of Bromium and Corey Kallenberg of The MITRE Corporation wherein “An authenticated local attacker may be able to bypass Secure Boot and/or perform an arbitrary reflash of the platform firmware despite the presence of signed firmware update enforcement”. If people don’t have awareness that attacks can be happening at this level then they’re going to have their guard down and an attack will be able to completely subvert their system.
Firmware is the software that sits behind the operating system and is used in all computers – whether they run Apple software or Microsoft’s Windows.
Thunderstrike 2 targets the option ROM on peripherals like Ethernet adapters and SSDs and spread by connecting an infected device to a Mac.
Firmware attacks are a favorite with the NSA.
In the video below, Hudson shows how an attack can jump from OROMs, to the BIOS, and back to the OROMs, primed to infect another Mac. The only way to recover from such attacks is to reflash the SPI flash chip with a known-clean copy of the firmware.
Apple has apparently been notified already and patched one of the exploits, with another partially fixed. Kovah also mentioned that usually EFI and UEFI are derived from the same reference implementation and also share the similar vulnerabilities. The company hasn’t yet commented on the effect of the Thunderstrike 2 worm. But Apple, for unknown reasons, has decided to ignore best practice from Intel.
Thus we can say that the components of Thunderstrike 2 is basically based on the vulnerabilities that were disclosed previously. Once these accessories are infected, they can spread to other Macs once plugged in.
Advertisement
“[The attack is] really hard to detect, it’s really hard to get rid of, and it’s really hard to protect against something that’s running inside the firmware”, Kovah said.