-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
Microsoft’s President Reflects On Cyberattack, Helping Pirates And The NSA
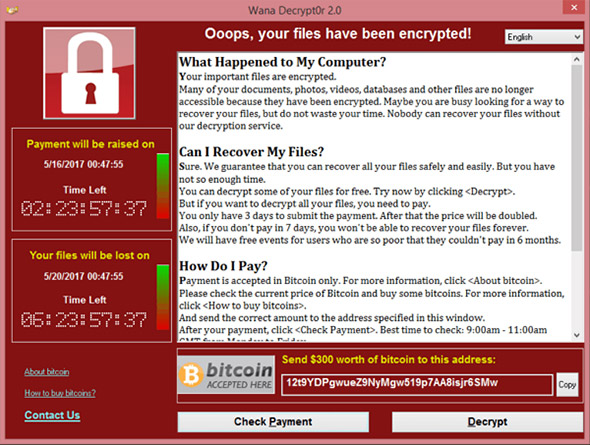
“A manual human operator must activate decryption”, revealed Matthew Hickey, a cyber-security researcher at UK-based firm Hacker House.
Advertisement
The message was circulated widely and has even reached Malaysian users, but has been rubbished by the Reserve Bank of India, who said they were keeping a close watch on the situation involving the WannaCry ransomware attack.
For many security experts who have been battling a rising tide of ransomware in recent years, the presumption was that Tuesday was simply a lull in what has become never-ending digital trench warfare.
“It leads me to think they did not think it would spread as far as it is”, he said.
Ransomware attacks are some of the most immediately damaging forms of cyber-attacks that affect home users, enterprises and governments equally. Reports indicate the hackers behind the WannaCry campaign are accessing enterprise servers either through a Remote Desktop Protocol (“RDP”) compromise or through the exploitation of a critical Windows SMB vulnerability.
By March, Microsoft had developed and distributed security fixes for the vulnerability. “It’s stopped more than 50,000 infections”.
The ransomware was temporarily blocked after its onslaught on Friday, but reports from several countries showed that the first series of attacks could be a start of more risky cyber intrusions.
“Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released”. The domain turned out to be a kill switch left in the code to stop the ransomware’s propagation.
Jonathan Levin is a co-founder of Chainalysis.
Businesses could face legal claims if they failed to deliver services because of the attack, said Edward McAndrew, a data privacy lawyer at Ballard Spahr.
Several sets of investigators have now reported tentative findings that suggest hackers linked to North Korea might have been involved with WannaCry.
“If anyone pays this ransom they are more than likely going to send Bitcoin that will sit in an address for ever more”.
Although nothing troublesome was reported on India’s ATM network, these machines are feared to be the most vulnerable to hacking as they still majorly run on the outdated Windows XP operating system.
The notion that the attack might have been launched by a nation-state, rather than a rogue criminal group, was no less comforting.
“The United States more than probably any other country is extremely careful with their processes, about how they handle any vulnerabilities that they’re aware of”, Bossert said. “Eventually, constraints on cyber espionage may be necessary, but these would only work if everyone observed them, and there is reasonable doubt that China and Russian Federation would go along”.
Many countries are racing to create more cyberweapons.
Code for exploiting that bug, which is known as “Eternal Blue”, was released on the internet last month by a hacking group known as the Shadow Brokers. Thus, responding to a ransomware attack should include an evaluation of relevant systems for the presence of other malware.
Advertisement
Microsoft President and Chief Legal Officer Brad Smith blamed the NSA’s practice of developing hacking methods to use against the USA government’s own enemies.