-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
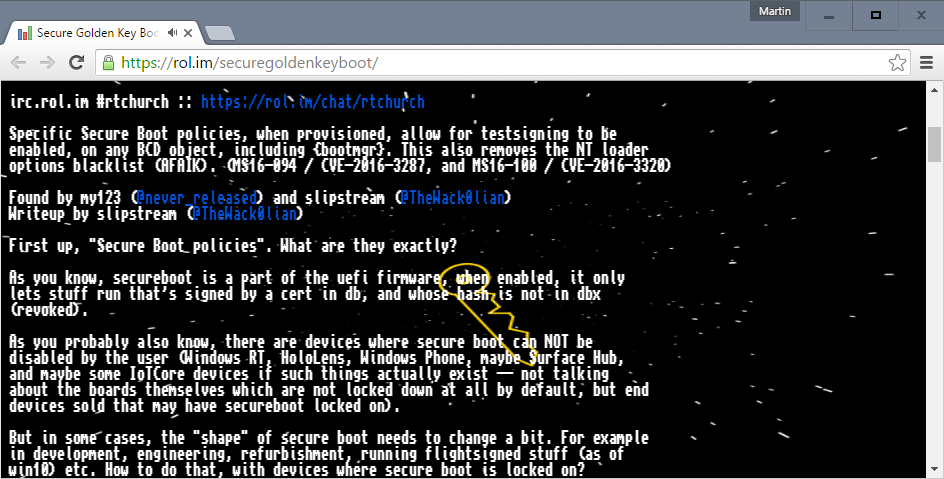
Microsoft’s Secure Boot design flaw exposed by security researchers
The feature basically prevented users from installing operating systems that aren’t signed by Microsoft – for example, if Secure Boot was enabled on your Windows 10 device, you won’t be able to install Linux on it. Advanced users can generally disable the feature from within the motherboard’s UEFI interface.
Advertisement
Secure Boot remedies the insecurities of the Standard Boot process. Secure Boot can be turned off on PCs and notebooks however, at least for the time being. Now, anyone looking to bypass Secure Boot is able to do so.
And perhaps most importantly: it is a reminder that demands by politicians and crimefighters for special keys, which can be used by investigators to unlock devices in criminal cases, will inevitably jeopardize the security of everyone. Any OS could be loaded, Windows or otherwise. For everyone else, it’s a serious security risk, although protections are in place to ensure the policy can’t be maliciously exploited.
To reiterate, these Microsoft-signed resources – the debug-mode policy and the EFI installation tool – are only meant to be used by developers debugging drivers and other low-level operating system code. The situation at that point was that since Microsoft controlled the key-signing authority, everyone who wished to boot an operating system on hardware certified for Windows 8 has to buy a Microsoft key.
Well now the key-disabling script is floating in the cyber ether; it would allow anyone with physical access to a Windows device, or admin rights, to bypass Secure Boot.
The researchers have now leaked the policy online. How it made its way into a public update hasn’t been confirmed. If you provision this onto your device or computer as an active policy, you’ll effectively disable Secure Boot. The mistake is being held up as an example of what could go wrong if the FBI’s requests for golden keys and back doors are granted.
But the keys release is nonetheless cause for celebration for many Microsoft device owners. “Secure boot makes sure that your PC boots using only software that is trusted by the PC manufacturer or the user”. If the golden keys were to leak out, any device could be unlocked by malicious actors.
“About the Federal Bureau of Investigation: are you reading this? If you are, then this is a ideal real world example about why your idea of backdooring cryptosystems with a “secure golden key” is very bad!”, the researchers explained in their highly technical write-up. “Smarter people than me have been telling this to you for so long, it seems you have your fingers in your ears”, writes Slipstream in the report. You seriously don’t understand still? For purposes of testing and tweaking, Microsoft has one boot policy that loads early in the process and disables the checks for operating systems. Should the Federal Bureau of Investigation or similar agencies demand that other technology companies create a secure golden key to subvert secure encryption systems, they open the field for those back doors to be exploited as well. Hopefully you can add 2+2.
Anyone who thinks government servers holding these keys are safe need only be reminded of the OPM megahack; anyone who thinks these keys can not be extracted from software or hardware need only spend a weekend with a determined reserve-engineer and a copy of IDA Pro.
Advertisement
Secure Boot was never really conceived as a way to protect YOU, it merely used the security excuse to protect the one thing Microsoft cares about: Microsoft. Microsoft is now trying to revoke the policy and recover from its mistake. Another patch is expected next week which will add more restrictions but still leave the rule usable.