-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
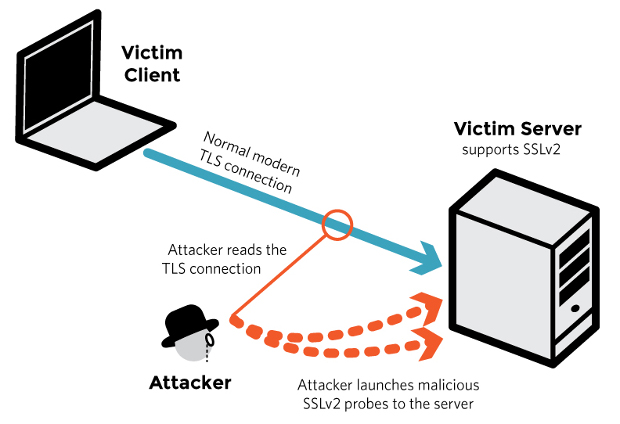
Millions of OpenSSL secured websites at risk of new DROWN attack
To defend against the attack, researchers advise you should ensure SSLv2 is disabled, or make sure that their private keye are not used anywhere with server software that allows SSLv2 connections.
Advertisement
Modern servers and clients use the TLS encryption protocol.
They said they had not released the code used to prove their theory because “there are still too many servers vulnerable to the attack”. However, many servers are misconfigured and still support SSLv2, a forerunner to TLS that was withdrawn from popular use due to major security flaws. With both DROWN and POODLE, an attacker is abusing the fact that servers sometimes still can enable support for older protocols alongside newer ones. Those vulnerable don’t need to re-issue certificates, but should take action to prevent the attack immediately.
A total of 15 experts from universities in the US, Israel and Germany contributed to a study which led to today’s publication of the paper DROWN: Breaking TLS using SSLv2, available here [PDF].
You can sniff data from an existing TLS connection, and then use it in a sequence of SSL 2 connections to the same server in the hope of figuring out the decryption key needed to eavesdrop on the original TLS connection.
Readers should understand the seriousness of the the vulnerability as nearly all of banks, financial institutions and other websites which gather personal identifiable information (PII) use HTTPS for secure communication between the user and the web server. It allows attackers to decrypt intercepted TLS communications if the 20-year-old SSLv2 protocol is supported on servers, a group of researchers has found.
The flaw, dubbed DROWN, could be used to access all kinds of sensitive information, the researchers, explained, in a detailed posting on a dedicated website explaining the flaw. That sounds like an obvious weakness in security, but it didn’t really matter up until now because no up-to-date software actually uses SSLv2 – apps and other programs tend to use TLS these days. These, in turn, can be used to unlock “secure” servers that use the same private key.
According to the researchers, the attack can be completed on a single core on commodity hardware in less than a minute, without GPUs or distributed computing, and is limited primarily by how quickly the server can complete handshakes.
The research indicates that a quarter of top-level domains deploying HTTPS and a third of all sites are vulnerable.
In any case, if you use OpenSSL for security, now is the time to upgrade to 1.0.2g. When taking key reuse into account, an additional 16% of HTTPS servers are vulnerable, putting 33 percent of HTTPS servers at risk. These “backdoor” ciphers have been legally unnecessary for more that a decade, and supporting them introduces the risk that an attacker could use 2016 computing power to attack ciphers that were deliberately chosen to be breakable more than two decades ago. The researchers have provided instructions on how to do that for some of the most common TLS libraries and Web servers.
Advertisement
“This form of the attack is fast enough to allow an online man-in-the-middle style of attack, where the attacker can impersonate a vulnerable server to the victim”, the researchers wrote.