-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
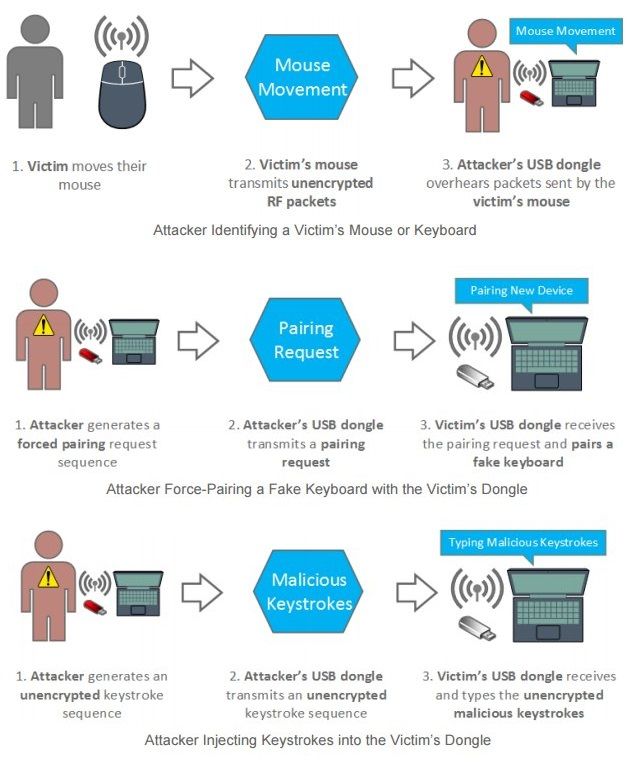
‘MouseJack’ allows hackers to hijack computers through your wireless mouse or keyboard
It’s common to have firewalls and other security measures protecting your PC’s network connections, but what about the wireless signal that your mouse uses?
Advertisement
Bastille, which tracks malicious Internet-of-things activities by using sensors to track the electromagnetic signatures of Internet-connected devices, determined that while data transmitted by wireless keyboards tends to be encrypted, none of the mouses it tested encrypted their clicks. Once infiltrated, which can be done with $15 worth of hardware and a few lines of code, a hacker has the ability to insert malware that could potentially lead to devastating breaches.
Researchers at Bastille Networks today said that non-Bluetooth devices from seven manufacturers including Logitech, Dell and Lenovo are vulnerable to so-called Mousejack attacks that would allow a hacker within 100 meters to abuse this attack vector and install malware or use that machine as pivot point onto the network.
“MouseJack poses a huge threat, to individuals and enterprises, as virtually any employee using one of these devices can be compromised by a hacker and used as a portal to gain access into an organisation’s network”, said Bastille’s founder and CTO Chris Rouland.
The method used to hack machines is called MouseJacking, and it potentially leaves billions of computers vulnerable to hackers. “What’s particularly troublesome about this finding is that just about anyone can be a potential victim here, whether you’re an individual or a global enterprise”.
What’s worrying is the large amount of wireless mice and keyboards that can’t be updated, thus rendering any hope of a patch useless. It does not affect devices that connect via Bluetooth.
After purchasing a cheap USB dongle and circuit board, a hacker can flash them with a clever Python script that Bastille made available on Github.
Advertisement
“Bastille Security identified the vulnerability in a controlled, experimental environment”, according to Logitech. Bastille’s recommendation is to disconnect them right away, and either push the developer to update the firmware, or simply buy from another vendor in the future. The vulnerability would be complex to replicate and would require physical proximity to the target. If your device is not listed, contact the manufacturer. The good news is that if you have Logitech peripherals, that company has apparently already patched its firmware against the Mousejack vulnerability. Users who connect to a wireless mouse in a public area like a coffee shop or airport are more likely to be at risk from a hacker lurking in the crowd.