-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
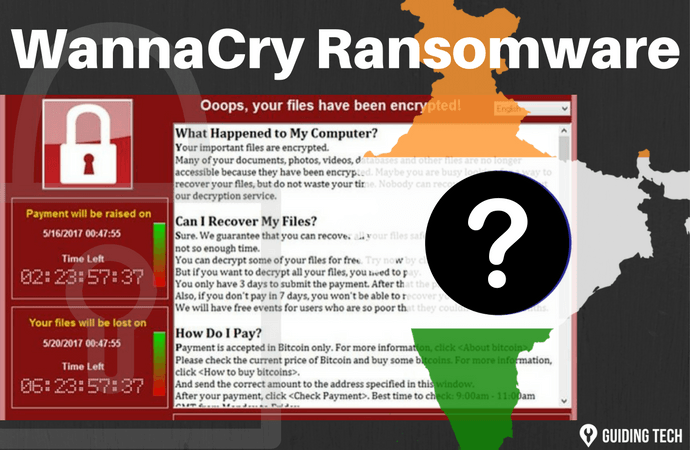
NSA ‘WannaCry’ hackers have ‘compromised’ data that could include foreign nuclear codes
A researcher from Google posted on Twitter that an early version of WannaCry from February shared some of the same programming code as malicious software used by the Lazarus Group, the alleged North Korean government hackers behind the destructive attack on Sony Corp.in 2014 and the theft of US$81 million from a Bangladesh central bank account at the New York Fed past year. With each new version of Windows, Microsoft warned that older operating systems would have security vulnerabilities that are not found on newer systems.
Advertisement
It’s hard not to engage in a bit of victim-blaming in this situation, especially because security experts say the attacks could have been prevented.
The cyber attack, described by Interpol as unprecedented in scale and which sought ransom payments valued at $300 (£230) and then $600 in the cryptocurrency bitcoin, should alert organisations that they face a crippling impact to their operations if they fail to take basic measures to protect the security of critical systems and data.
Experts cautioned, however, that the criminals who pushed the ransomware to the world might be able to disable the “kill” switch in future versions of their malware. The report quoted State Bank of India Officers’ Association Secretary General R. Ramesh as saying, “Ransomware attack appears to be causing glitches at many ATMs that work on Random Access Memory (RAM)”.
Ransomware was already becoming a higher priority before the WannaCry epidemic of last week, but it’s clear that it has now made the shift from nuisance to serious threat. The researcher claims that the tool can decrypt files encrypted by WannaCry ransomware files and the underlying idea is the same as implemented by Guinet.
“We encourage all Dedicated and VPS customers to ensure they have antivirus software; a data backup solution; and regularly update all software, including the operating system, on a regular schedule”, Raven concluded. Brad Smith, Microsoft’s chief counsel, said Sunday in a company blog post that the practice of hoarding so-called zero-day exploits (so called because it’s not publicly reported or announced before it is used) leads to attacks like WannaCry. The worst hit so far: people using Windows 7. Users that haven’t yet applied the update should immediately deploy the necessary fix, he added.
But a programme and its source code under public scrutiny can identify the loopholes in the system and patch immediately before crackers exploit that vulnerability. Microsoft still installed these modules in the PCs and activated them. “(Which is a shame, because that would have meant computers would have been patched earlier)”. By taking a decision to migrate from proprietary operating system to a GNU/Linux operating systems, you are not only staying safe but also become part of culture and community who believe in sharing and collaborating.
“The NHS wasn’t targeted”, he wrote. While acknowledging the importance of consultations between the United States and China, he said that they are unlikely to be able to solve the problem given the two countries’ diametrically different interests in this area.
Advertisement
Personally, I know many I.T. Security analysts. The employees in that company’s tech department are leaving constantly – and at a rapid pace – due to the mismanagement. As a result – the company is now at a high risk for invasion.