-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
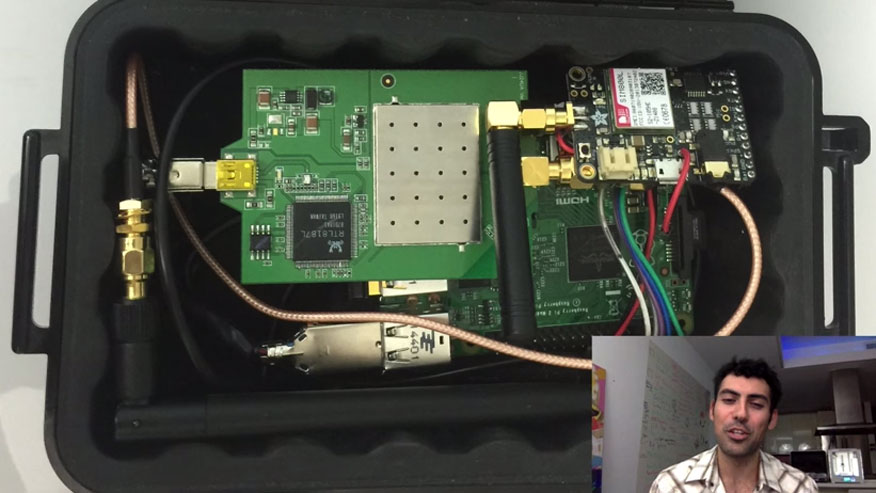
OwnStar Attack Now Aimed at BMW, Chrysler, Mercedes Cars
Samy Kamkar, the white hat hacker who discovered a security hole in GM’s OnStar app a couple of weeks ago that he could use to remotely track, unlock and start practically any vehicle using the system, has found the same issue in apps from four other brands, Wired reports. Kamkar built a Raspberry Pi-based device he calls OwnStar to execute the attack, which he demonstrated originally against the GM OnStar RemoteLink app. The device can intercept the traffic, send special packets to the device, gain credentials and then locate, unlock, and start the victim’s vehicle. But Kamkar has now updated his OwnStar device to also intercept the credentials of BMW, Mercedes-Benz, Chrysler, and Viper’s apps. Kamkar told Wired, “If you’re using any of these four apps, I can automatically get all of your login information and then indefinitely authenticate as you”.
Advertisement
According to the hacker, the different manufacturers use very similar methods to enable the auto and the app to communicate.
Kamkar won’t be releasing the updated code for OwnStar for at least 30 days so the automakers have a chance to update their systems. He wants to give the companies an opportunity to fix their security problems like GM did previously did with OnStar. He added that “to our knowledge, there has not been a single real world incident of an unlawful or unauthorized remote hack into any FCA vehicle”.
We have contacted both Mercedes and BMW for a comment on this vulnerability. Chrysler responded with a recall of 1.4 million vehicles. “Unfortunately it’s prevalent among half the other mobile unlocking apps I’ve tested”, Kamkar said.
Advertisement
“The vulnerability that the researcher claims to be able to exploit relates to the mbrace app which is unique to the U.S”, said a Mercedes spokesperson. “We’re really only scratching the surface of the security of these vehicles”, Kamkar says.