-
Tips for becoming a good boxer - November 6, 2020
-
7 expert tips for making your hens night a memorable one - November 6, 2020
-
5 reasons to host your Christmas party on a cruise boat - November 6, 2020
-
What to do when you’re charged with a crime - November 6, 2020
-
Should you get one or multiple dogs? Here’s all you need to know - November 3, 2020
-
A Guide: How to Build Your Very Own Magic Mirror - February 14, 2019
-
Our Top Inspirational Baseball Stars - November 24, 2018
-
Five Tech Tools That Will Help You Turn Your Blog into a Business - November 24, 2018
-
How to Indulge on Vacation without Expanding Your Waist - November 9, 2018
-
5 Strategies for Businesses to Appeal to Today’s Increasingly Mobile-Crazed Customers - November 9, 2018
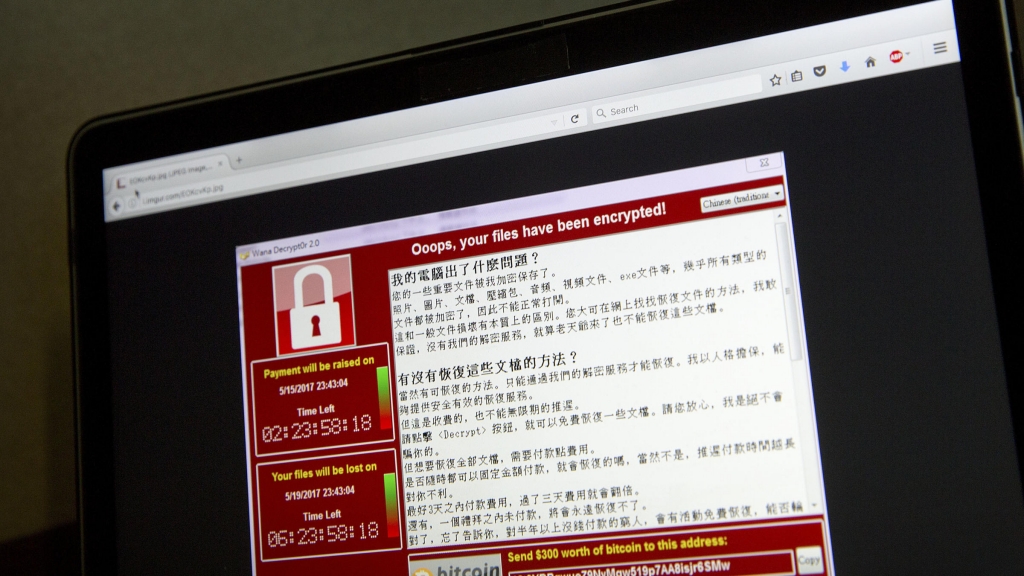
Ways to Become a Smaller Target for Ransomware Hackers
Microsoft has already issued Customer Guidance on this, urging Windows users to apply the relevant security updates that patch this flaw and protect them from the WannaCry ransomware attack. And many computer networks, particularly those in less-developed parts of the world, still use an older version of Microsoft software, Windows XP.
Advertisement
His concerns were echoed by James Clapper, former director of national intelligence under President Barack Obama.
The BBC broadcast a screen-shot of a message apparently sent to the National Health Service medical facilities demanding payments for unlocking computer files that had been “encrypted” by the attack.
The 22-year-old researcher known as “MalwareTech”, who wanted to remain anonymous, said he spotted a hidden web address in the “WannaCry” code and made it official by registering its domain name.
“Since the global coordinated ransomware attack on thousands of private and public sector organisations across dozens of countries on Friday, there have been no sustained new attacks of that kind”, the NCSC said.
But, if everything is backed up, the encrypted files are not as valuable to the attackers. “Even without having an antivirus”, they said.
Hospitals are also fertile ground for identity thieves due to their often-lax security policies. With this attack, Abrams recommends trying to recover the “shadow volume” copies some versions of Windows have. Meanwhile, you should make sure your OS is up-to-date.
Critical infrastructure agencies including banks, airports, telecom networks and stock markets have been asked to take precautions to shield themselves against the crippling global ransomware attack “WannaCry”.
The latest ransomware was successful because of a confluence of factors.
While any sized company could be vulnerable, many large organizations with robust security departments would have prioritized the update that Microsoft released in March and wouldn’t be vulnerable to Friday’s attack.
This security update resolves vulnerabilities in Microsoft Windows.
As similar widespread ransomware attacks were reported in Spain, Romania and elsewhere, experts warned that online extortion attempts by hackers are a growing menace. “I hope that if another attack occurs, the damage will be a lot less”. While a United Kingdom security researcher managed to stop the spread of the virus, hackers have issued new versions that cybersecurity organizations are trying to counter and stamp out. “You’re only safe if you patch ASAP”. But many corporations don’t automatically update their systems, because Windows updates can screw up their legacy software programs.
The stock market has reacted, causing shares to surge in security technology firms, and it is believed that the attack will lead to more sales of security products.
Europol said a special task force at its European Cybercrime Centre was “specially created to assist in such investigations and will play an important role in supporting the investigation”.
Basic protocol such as stressing that workers shouldn’t click on questionable links or open suspicious attachments can save headaches. Old software, older hardware and other problems make it very hard for IT departments to have much say in system upgrades. This helps limit the spread of ransomware if hackers do get into your system.
Monday was expected to be a busy day, especially in Asia which may not have seen the worst of the impact yet, as companies and organizations turned on their computers. Affected users can restore their files from backups, if they have them, or pay the ransom; otherwise they risk losing their data entirely. There’s also no guarantee all files will be restored.
Advertisement
The non-profit U.S. Cyber Consequences Unit research institute estimated that total losses would range in the hundreds of millions of dollars, but not exceed $1 billion. So far, he said, not many people have paid the ransom demanded by the malware.